“If it ain’t broke, don’t fix it!” That saying applies in many places, but NOT to computer hardware and software. It’s clear that many of today’s cyber attacks prey on
Financial losses, data breaches and reputational damage are just some of the ways a cyber-attack can hit an organization hard. The Petya and WannaCry cyber-attacks in May and June 2017
Most small business owners don’t know much about basic computer maintenance and as a result, their PCs slow down or crash. The real issue is neglect: failing to update security
Computer virtualization has been rising in popularity during the past few years due to its ability to provide a viable solution for companies to increase productivity while reducing IT infrastructure
If you’re looking for a competitive IT advantage, maybe it’s time to look at partnering with a managed service provider (MSP). These trusted IT partners work in conjunction with your
Here are six things you should do to help keep your personal information safe and secure. Use a VPN on public networks. You may not know this, but the public
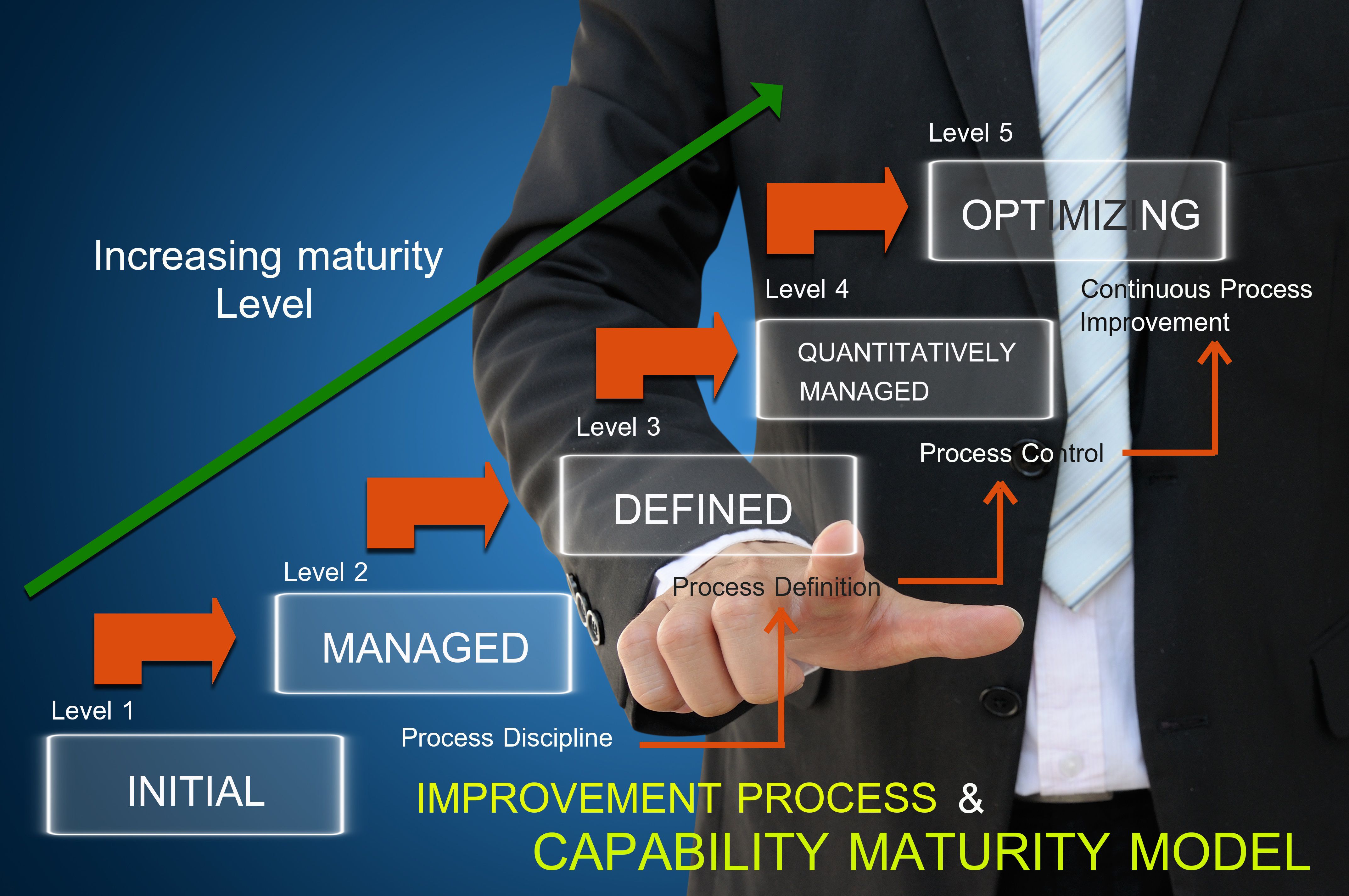
Understanding Maturity Levels To support those who use the staged representation, all Capability Maturity Models(CMM) reflect maturity levels in their design and content. A maturity level consists of related specific
A study from the National Institute of Standards and Technology (NIST) found that 63 percent of participants have experienced “security fatigue,” defined as “a weariness or reluctance to deal with computer security.” It’s not
Who’s ready to fight cybercrime in 2018? Don’t all raise your hands at once. If you’re a CIO or CISO, you’re expected to provide cybersecurity and Protect sensitive data.
Healthcare organizations have become very acquainted with the HIPAA Privacy Rule over the last few years. Privacy officer appointments and employee training have become ubiquitous ever since the Omnibus Rule